In October, I reported two security issues to Okta’s auth0/nextjs-auth0 project, here and here. The latter bug, an oauth parameter injection, allows for a range of types of abuse, like scoping tokens for unintended services, setting redirect_uri and scope to arbitrary values to leak tokens, and so on.
The patch was simple enough, so I opened a PR:
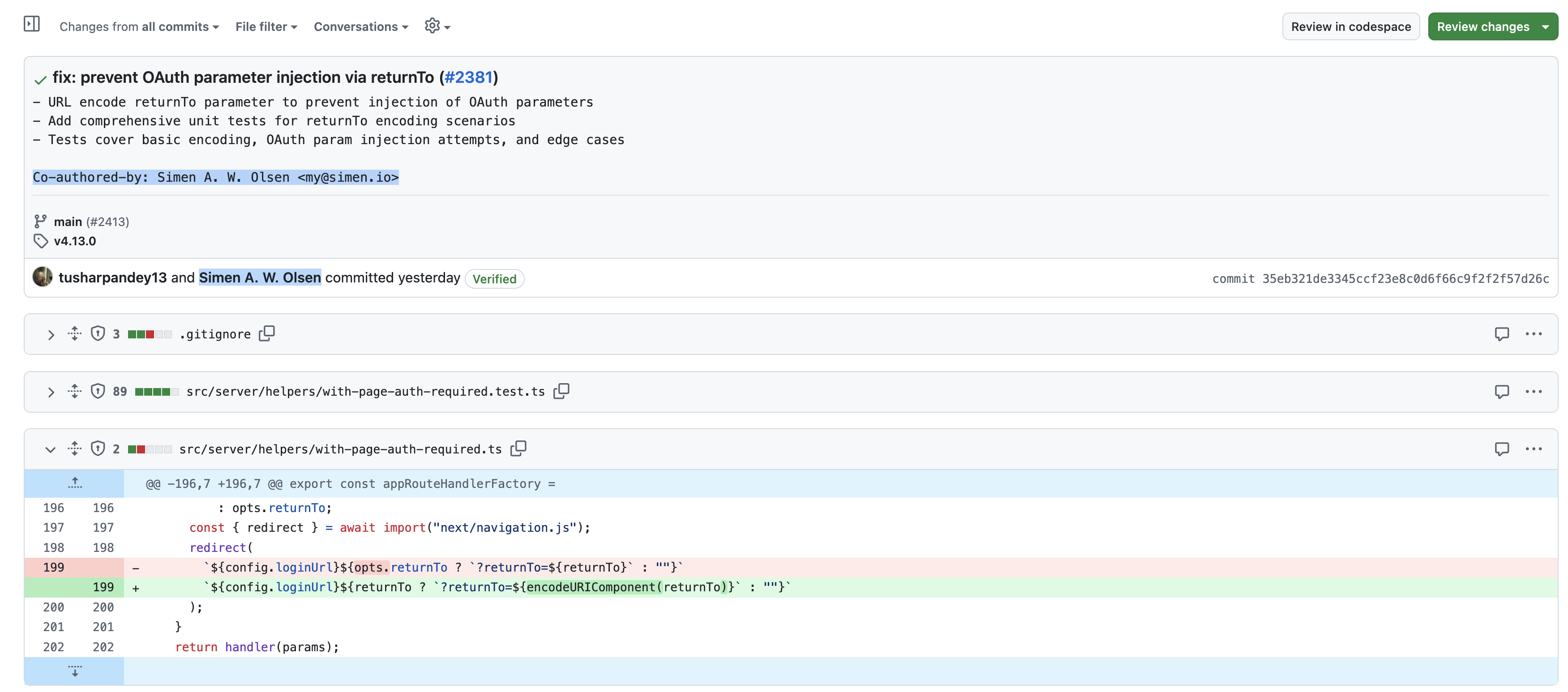
diff --git a/src/server/helpers/with-page-auth-required.ts b/src/server/helpers/with-page-auth-required.ts
index 41af2dfe..f07046b8 100644
--- a/src/server/helpers/with-page-auth-required.ts
+++ b/src/server/helpers/with-page-auth-required.ts
@@ -196,7 +196,7 @@ export const appRouteHandlerFactory =
: opts.returnTo;
const { redirect } = await import("next/navigation.js");
redirect(
- `${config.loginUrl}${opts.returnTo ? `?returnTo=${returnTo}` : ""}`
+ `${config.loginUrl}${opts.returnTo ? `?returnTo=${encodeURIComponent(returnTo)}` : ""}`
);
}
return handler(params);
All’s well that ends well, right? Obviously, no.
The PR, 3 weeks later, was closed by the maintainer, an auth0 (an Okta company) employee, with the following comment:
This change is superseded by #2413. This was done to ensure that commits are signed. Orignal contribution history has been preserved. Hence closing this PR now.
Hmm, let’s take a look at that PR:
 |
|---|
| auth0/nextjs-auth0 #2413 |
Hmm. That patch looks familiar. And who is Simen Olsen?
Pushing back on the attribution error, I replied:
history has been preserved
no it hasn’t. I don’t know who “Simen A. W. Olsen my@simen.io” is but it isn’t me and my commit here doesn’t reference that name or email address at all. Was it ai generated or something?
Of course, the answer was: yes. It was AI slop. Just like my previous post about gixy-ng (a fun read for anybody dealing with nginx), the developer had used CoPilot to somebow generate their patches:
Hi @MegaManSec I sincerely apologize for this attribution error.
Can confirm that an AI workflow was used to created the rebased commit, which got confused with OP details. I’ve added a correction to #2413, and will ensure the changelog is updated.
Thank you for calling this out, we’ll make sure this doesn’t happen again.
Not only did the maintainer state the above, they also used AI to generate the response! In a now-deleted comment, they clearly used some AI to respond to my complaint:
 |
|---|
| auth0/nextjs-auth0 #2413’s now-deleted comment |
With the classic ChatGPT “you are absolutely correct”, it’s pretty frustrating that this developer used AI to:
- Take my report/PR and commit it themselves.
- Used AI to commit it, removing my attribution.
- Used AI to “apologise” for using AI, then stated that “it won’t happen again” – (yeah right; please provide a detailed explanation how you’re going to ensure that, when clearly a 1-line code change is too much for your AI to handle without breaking).
- Refused to fix the commit to remove the invalid / AI-generated-slop details, and add back mine.
Indeed, asking:
I would appreciate force-pushing a fix for the commit to properly include my information in the commit.
I was told that they cannot change it. That seems like a copyright infringement to me: taking somebody else’s code, then changing the author’s name?
What I really find the most interesting is really how this AI slop even came to be. I cannot find any reference to the email address “my@simen.io” anywhere online. On GitHub, the only reference to this email address is from the nextjs-auth0 PR. Simen Olsen has never contributed to any of the nextjs-auth0 repositories as far as I can tell (searching org:auth0 author:simenandre on GitHub), and that doesn’t even seem to be their real email address. so was this some type of ai hallucination? And why? The code change was tiny. I just totally don’t get it: I have literally never had any AI tooling fail like this and come up with some other person’s (fake) contact details. It’s simply absurd; are auth0’s engineers using some extremely (extremely) low quality local model or something? If ChatGPT failed like this for me even once every thousand times, I would simply never use it again.
In the end, at the time of writing this, the auth0/nextjs-auth0 maintainer, Tushar Pandey, who made all of these mistakes, has not fixed attribution mistake in the commit history. In addition to this, that first bug, which allows for arbitrary account hijacking in this software, has been fixed after 3 weeks, with new versions of the nextjs-auth0 software released, but Okta’s security people stating that “unless you create a video abusing this vulnerability, we aren’t going to accept this as a security issue” – LMAO; “yeah, it’s a vulnerability, we fixed in the code, it can be used to takeover accounts, but you need to create a video”. Hilarious. That’s just another case to add to my list of hilarious problems related to reporting security issue, that my next post will document.