In a previous post where I discussed an account persistent exploit for Google accounts, I mentioned that the whole ordeal has reminded me of an old exploit in RuneScape which allowed an attacker to: attempt logging into an unlimited amount of accounts with no restriction, access in-game bank accounts bypassing their in-game pin-code, and another related bypass.
In this post, we’ll see how sitting on a vulnerability in private is vastly more profitable than.. selling it to others on a subscription-based basis.
First release in late 2013, the RuneScape Companion was a peripheral application that allowed players to use a small subset of functionality in the game without launching the full application (which required a full Java client). RuneScape is a massive game, and the Companion provided a convenient way to not play the game in of itself, but perform some minor actions like: chat with your friends and clan chats, view the contents of your bank, and buy/sell items in the grand exchange (the game’s centralized ‘stock market’ for in-game items). If you just wanted to buy and sell things or chat with friends, the Companion was a lightweight solution which was not only available in the browser, but also as an app on iOS and Android. Apparently it was also available for the thirteen people that used a Windows Phone.
The first slide (from the left) of the below image from the iOS Companion App shows the login screen. The second slide shows the different functionality of the app. The third slide shows a user accessing their bank and seeing the different items they have and total gold pieces (gp). The fourth slide shows the buy and sell functionality in the grand exchange.
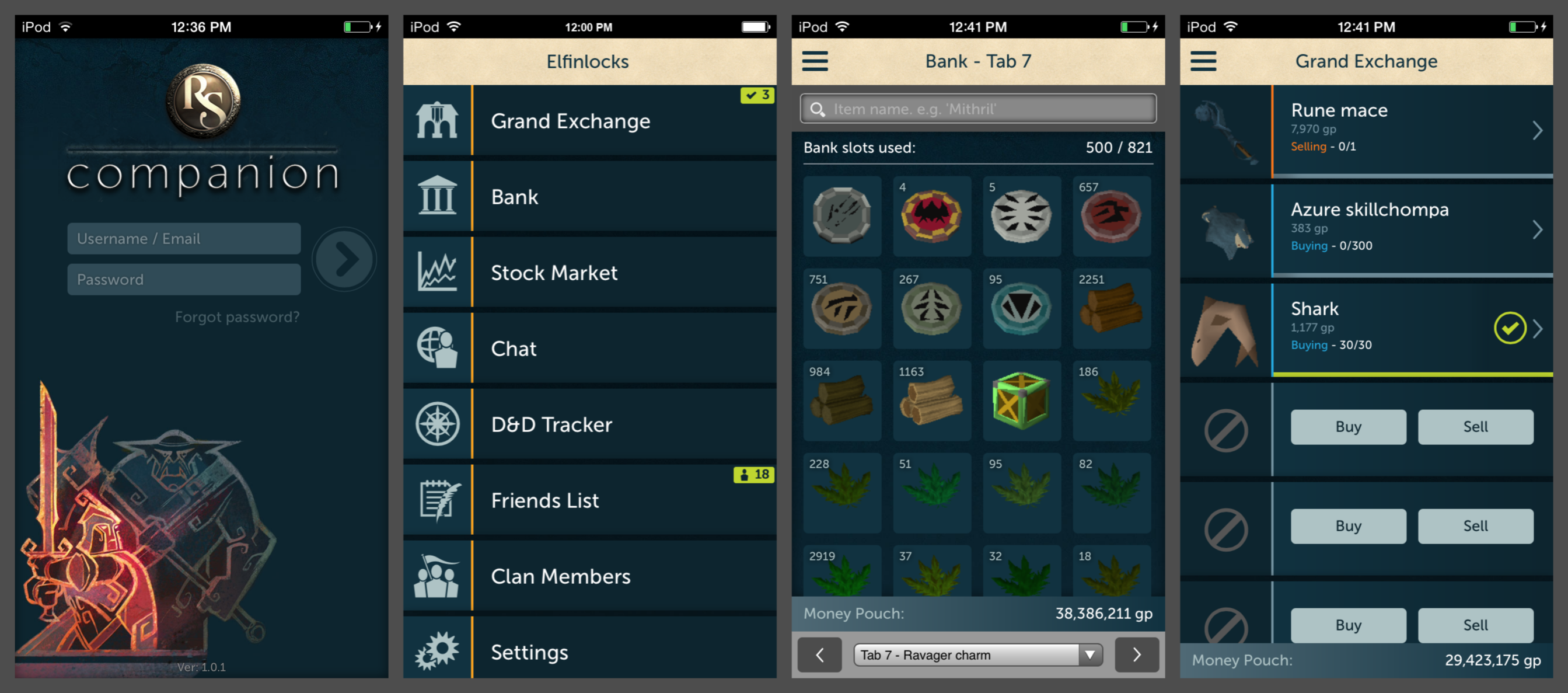
Like most apps that were released around that time (“why don’t we have an app?” – management, probably), the Companion app’s approach to access violated the trust boundary which the game had previously used – not only did the app have its own issues, but the app’s existence introduced vulnerabilities into the main RuneScape game.
Back in 2013, credential stuffing (or as we called it, “checking” or “cracking”) was all the rage: we were dumping forum databases like it was a national sport and setting up multi-GPU cracking rigs like we were trying to trying to take over the bitcoin network (ironic, since we’d all be billionaires if we had mined bitcoin using the GPUs then). Using compromised logins from one location to try to login to another nearly guaranteed a hit back then. Likewise, 2-factor-authentication was rare, so once you got access, you could do whatever you wanted. “Whatever you wanted” back then was generally: access an administrative panel to get access to a new database, a hosting service desk to get root access on a server, or access some account somewhere to siphon off the currency which could then be sold for real money (I didn’t know anybody hacking real life bank accounts).
Account checking on RuneScape was difficult, because an ip-based block was activated after two invalid login attempts. To this day, the RuneScape website doesn’t support IPv6: although this is probably more related to technical debt than security, it wouldn’t surprise me if it was also related to the fact that if IPv6 were supported, it would make account checking extremely easy (4294967296 ipv6 addresses are like 50 euros a month). That’s where the RuneScape Companion came in.
The RuneScape Companion was fundamentally flawed: it allowed for an unlimited amount of login attempts, and did not force any captchas. I’m not sure why it didn’t use captchas despite various failed login attempts, but it was a cracker’s dream. Using a simple script, you could take your list of username:password combinations, and easily check thousands of logins every minute. No proxies were needed at all, and it was as easy as sending an HTTP request to the RuneScape server with a username and password value.
This vulnerability was known at least in my private circle for a few months before it was discovered (or leaked to?) by somebody else. They had heard about the possibility of being able to check an unlimited amount of accounts without a captcha, and went off to discover the vulnerability themselves. Loose lips sink ships, and the mere knowledge of the existence of the vulnerability was enough for it to be found by somebody else. What’s worse, is that this person decided to sell access to the vulnerability. He set up a website which other people could upload their username:password lists, and it would then spit out the valid accounts. “Proxyless runescape checker” it was advertised as. I don’t remember exactly how much this service was sold for, but I think it was about $50/month.
After this service was publicized, the bug was patched very quickly. Of course. The seller must have made only a few hundred dollars. The people abusing the bug made hundreds of thousands of American dollars (in-game RuneScape gold has quite a high real-life price). A true travesty. An amazing vulnerability burnt for.. a few hundred dollars.
If the seller of this service had just abused the vulnerability himself, he could have also made tens or hundreds of thousands of dollars. If the existence was never revealed (to either the world or even to him) it would would have.. well.. sigh..
The Companion app didn’t just allow for brute-forcing/cracking/checking accounts. It also had multiple other fundamental flaws: it could be used to bypass 2-factor-authentication (Google Authenticator), in-game pin-codes code bank accounts, and most importantly, be used to steal in-game items and gold (using the former two vulnerabilities).
In RuneScape, you can store your items in an in-game bank (which, if you die, you don’t lose, like the items you’re carrying). You can also set an in-game 4-digit pin which is required once when you access your bank account the first time after logging in. This pin is supposed to protect you from hackers: if you do get hacked, they can’t access your bank account. Instead, they can request for it to be removed from the bank – but this process can either take 3-days or 7-days (depending on what the user sets the recovery delay as).
Back then (and is probably still true), it was quite easy to hack active players; either through the aforementioned credential stuffing, or abusing RuneScape’s “forgotten password” feature which you could provide details about your account (like when it was created, location it was created, previous passwords (which could be guessed from database dumps), and so on) and a RuneScape employee would review the request, possibly resetting the password for you. You’d think this would never work, but this was one of the most successful ways to hack RuneScape accounts, and even the most famous players were popped like this – even if they had logged in just yesterday! This process was/is known as “recovering”; basically it’s just social engineering facilitated by RuneScape’s support team’s (deliberate?) negligence (incompetence?). It also certainly helped if you had a girlfriend working in the team that accepted or denied those requests.
The bank pin recovery delay was a big issue for hackers, because hacking any account with possibly thousands of dollars worth of in-game gold would be impossible unless the player didn’t login for a few days (which is rare?) So a pin bypass was a big improvement.
The vulnerability wasn’t complicated at all: you could change a localStorage value that restricted access to the bank account – basically, you just told the server “yes, I have already entered my bank pin” and it trusts you. This also meant the server wasn’t tracking whether the pin had been entered correctly. Looking back, I wonder whether it was possible to actually obtain the pin using this method, instead of bypassing it. I also don’t know – after it was patched – whether anybody tried to see what would happen if you attempted actions by calling the appropriate javascript function (maybe they “fixed” the pin validation, but actions which you could perform in the bank were still possible?)
This made a lot of people a lot of money. Some had been sitting on famously rich players’ login credentials for years, without a way to access their bank account. Others.. sold the method for a few hundred dollars. It was patched not soon afterwards.
Another once-in-a-lifetime vulnerability patched for a few thousand dollars of sales. A true travesty.
RuneScape accounts can also be set up with 2-factor-authentication. In order to login to the game at all, you need to authenticate using Google Authenticator. The RuneScape Companion App was no different: to login, you needed to use 2-factor-authentication. However, like the in-game bank pin-code, you could simply switch a local Javascript variable to pretend you had successfully authenticated with the 2-factor-authentication code.
Up until this point, some people already knew the login credentials for some of the most famous and most rich accounts in the game: they could try to login, but they wouldn’t be able to get past the authenticator page (which did not alert the user that somebody had successfully logged in but failed the authenticator phase). Years worth of username and passwords which couldn’t be used to enter the game had been collected, and this was finally an opportunity to siphon off the in-game items.
This was sadly leaked and patched at the same time as the pin bypass. Some people made upwards of a million dollars with this, since they had the credentials for extremely rich and famous accounts for a long time.
There was apparently another 2-factor-authentication bypass related to the Companion App, but I cannot confirm whether it was real or not. An old text from the successor forum of mine, abusewith.us (whose owners were arrested and charged with running another hacking website and were highly likely behind the Ashley Madison hack), purports to reveal information about that exploit. For historical purposes, I’ve uploaded the text from that post in a text file here.
Logging into the companion app with the stolen credentials, changing the local variable to bypass the authenticator requirement, and changing the local variable to bypass the bank pin; it was a hackers’ dream. All layers of protection that could be added to an account were stripped away. But then, once you did all of this, how did you actually steal in-game items, given that the companion app couldn’t actually be used to trade items with other players? Normally to steal in-game items or gold, you would have to trade the items to another player. You couldn’t trade in Companion App, but you could buy and sell items in the Grand Exchange (it is common in-game to buy/sell items to make profit, known as “merching” (merchanting)).
The Grand Exchange is a centralized market where players can buy and sell items. If a buyer puts an offer of 200gp and a seller puts it on the market for 100gp, the seller receives 200gp (buyer first offers too much; the seller is rewarded). If a seller puts an item on the market for 100gp and a buyer puts an offer for 200gp, the buyer receives the item and 100gp back (seller first sells for too little, the buyer is rewarded).
By abusing the first mechanic, hackers could siphon off the collective wealth of accounts. A hacker found some obscure, cheap item that is generally not bought or sold on the Grand Exchange, and offered (from their own account) to sell it for the an insanely high amount of in-game money (the same amount of money that the hacked account has). Normally, this item would never sell for this price, but the hacker would then go on the hacked account and make a purchase for that item – setting the price they are willing to pay for it as the insanely high amount of in-game money they are selling the item from their own account. To reiterate simply: the hacker would sell a cheap obscure item in the Grand Exchange for a large amount of money, and the hacked account would buy it.
First, of course, the hacker had to sell all of the items in the hacked account’s bank for gold; simple enough. However, this also meant that for insanely rich accounts which had some items worth more than the maximum amount of money that the game can handle (2^31-1 or 2147483647 gp), the hacker lost some money. In RuneScape, there are rare items which by themselves are worth more than the maximum allowed in-game gold pieces; when the hacker sold them on the Grand Exchange, they received the maximum value of 2147483647 – much lower than the real market value (whoever ended up buying that item, for which there would have been a lot of buyers waiting for the day they could get such a great day, would have been overjoyed.)
This was never “fixed” because it wasn’t really a bug – it was just how the game worked, of course. It was known in a few circles, but it wasn’t considered a secret, since it could not ever be patched without the functionality just being removed (and then, what would the point of the Companion app actually be? In-game chat only?)
Once again, putting it all together:
- Hack accounts using the captcha-less login with credential stuffing, or some other way (and there are lots!),
- Bypass the 2-factor-authentication by changing a single Javascript variable,
- Bypass the in-game pin by changing a single Javascript variable,
- Sell all of the items from the bank,
- Buy an uncommonly-sold item for a massive price – and sell that item from your own account for that massive price,
- ???
- Profit!
Two screenshots of somebody exploiting this, where they have hacked the most famous player in RuneScape shows how easy it was.
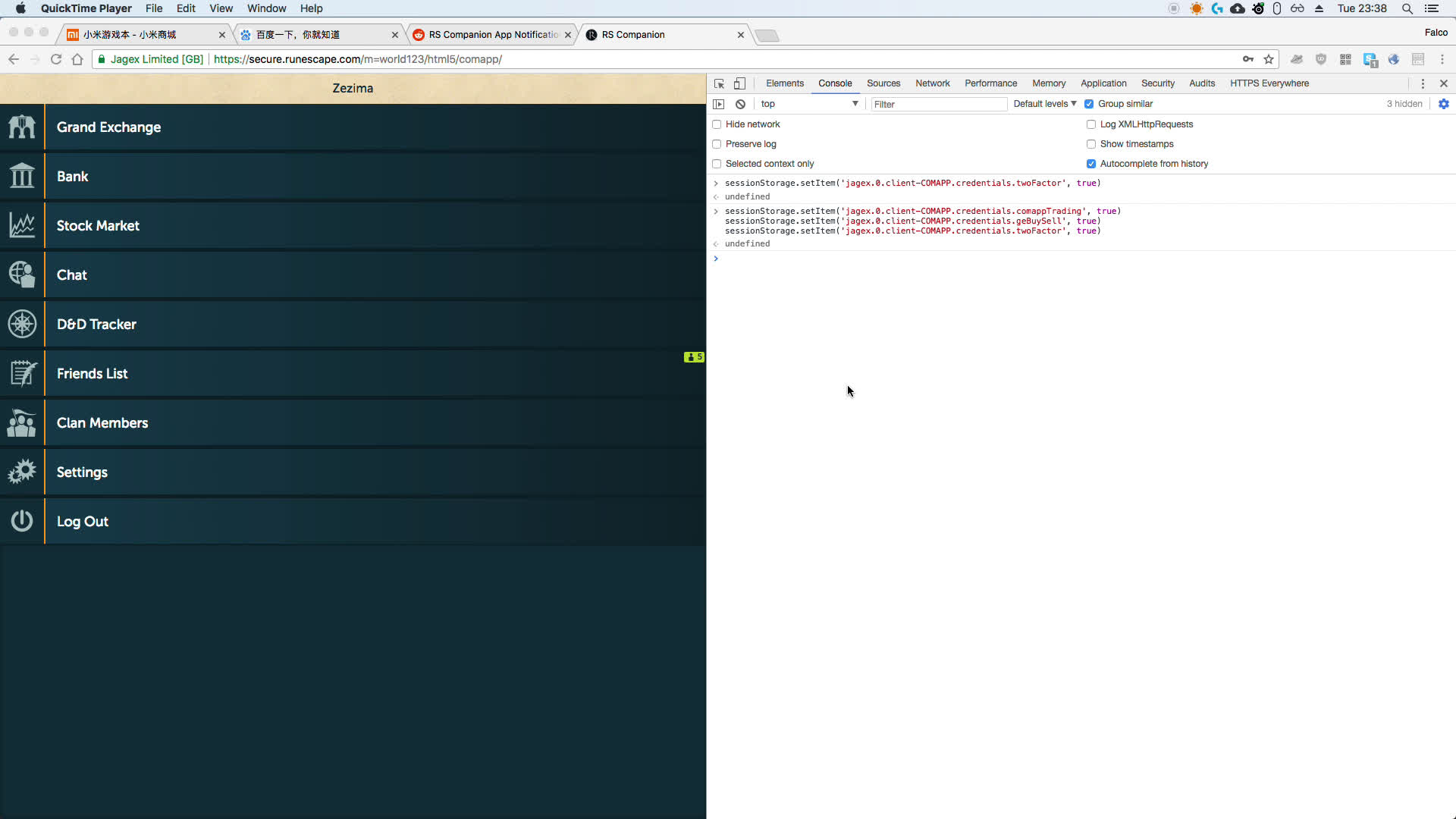
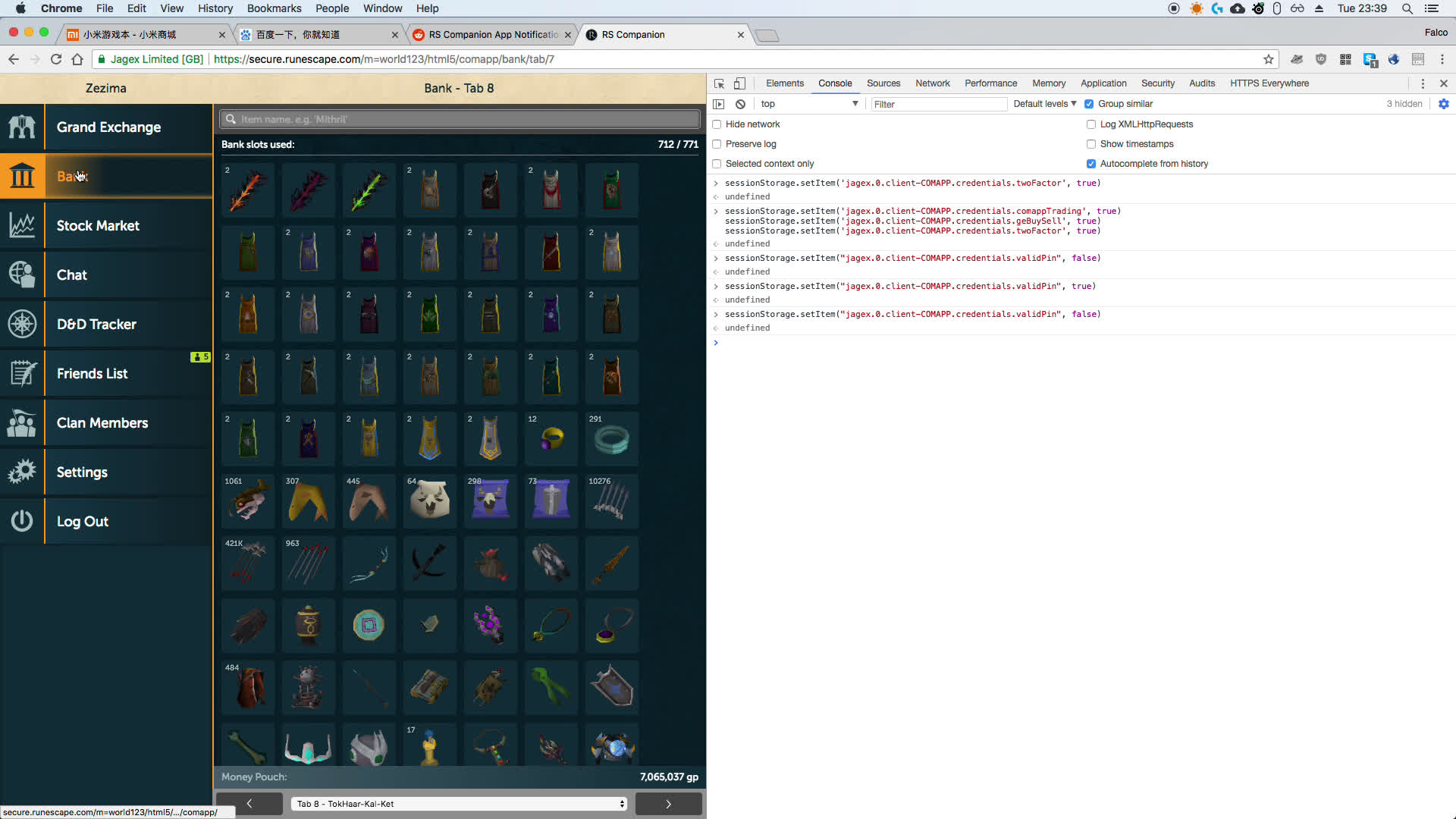
Note the commands in the dev console.
The moral of the story is that sitting on hacked accounts, exploits, or other secrets for a long time is a good investment. You can only really tell anybody of these things (even “just one person!”) if you’re willing to accept that it means you will lose what you have – you have to just assume that telling anybody automatically assumes you’ve lost access; whether it happens the first time, second, or third, it’s just an assumption that you have to make. If somebody knows of the existence of a bug, it always plays out the same as leaking the bug itself.
Also maybe alert people that somebody tried to login to their account but didn’t pass the 2-factor-authentication stage.